Card testing used to sit in an awkward corner of fraud operations. Everyone knew it existed, most teams dealt with it periodically, and as long as nothing settled and chargebacks stayed flat, it rarely triggered serious concern. It was noisy, irritating, but manageable. Something you cleaned up and moved on from.
By 2026, carding, especially BIN-range testing, has become a merchant acceptance problem, not just a fraud one. Schemes see it. Acquirers are accountable for it. And merchants are increasingly judged on whether their checkout environments quietly enable testing, even when no money is lost. The uncomfortable truth is that nothing bad happened is no longer a defence when your traffic patterns tell a different story.
What’s changed is not just attacker behaviour, but visibility. BIN attacks don’t need to succeed to matter anymore. Repeated failures, thin authorisations, and unnatural retry behaviour now create measurable signals upstream. Once those signals surface, conversations with acquirers shift quickly from curiosity to expectation, and then to pressure.This blog is written for merchants who don’t want to learn that lesson the hard way. It’s not a technical manual and it’s not a vendor pitch. It’s a practical, 2026 relevant defence narrative: how card testing actually shows up today, why traditional controls often miss the point, and how merchants can design payment flows that stop BIN attacks before they become an acquirer problem.
- What Carding Actually Looks Like in 2026 (Not the Old Mental Model)
- Why BIN Attacks Trigger Acquirer Attention Faster Than Before
- Early Warning Signals Merchants Miss Until It’s TooLate
- Why Traditional Fraud Rules Don’t Stop Card Testing
- The Merchant Defense Playbook Without Turning This Into a Manual
- Preserving Conversion While Blocking Testers
- Stopping BIN Attacks Before They Reach Your Acquirer
- What to Document When Card Testing Happens
- Conclusion
- FAQs
What Carding Actually Looks Like in 2026 (Not the Old Mental Model)
When people think about carding, they still picture the obvious version: bursts of tiny authorisations, strange product choices, and traffic that looks nothing like real customers. That version still exists but it’s no longer the dominant pattern merchants need to worry about.
In 2026, most card testing is deliberately boring. Attackers aren’t trying to trip alarms anymore. They’re trying to blend. Instead of hammering one endpoint, testing is spread across time, devices, sessions, and sometimes even different parts of the checkout journey. Individual attempts look unremarkable. It’s the shape of the traffic that’s wrong, not any single transaction.
Another shift is intent. Modern carding isn’t optimised for approvals. It’s optimised for learning. A decline is often just as valuable as an approval if it confirms which combination didn’t work. That’s why many attacks never aim to clear or settle at all. The goal is to map the credential space, not to cash out immediately.
This also explains why card testing now frequently hides inside what looks like legitimate low-value commerce. Normal basket sizes. Normal timing gaps. Even normal-looking user agents. The attack doesn’t announce itself; it reveals itself slowly through repetition and correlation.
For merchants, this creates a dangerous illusion. Fraud dashboards stay quiet. Chargebacks don’t move. Everything feels fine. But underneath, the checkout is quietly doing exactly what attackers want, responding consistently, retrying predictably, and confirming state with every interaction.
That’s why the old mental model breaks down. Carding in 2026 isn’t loud, fast, or greedy. It’s patient, distributed, and analytical. And if your defences are built to catch obvious spikes instead of behaviour that doesn’t map to genuine purchase intent, you’ll miss it until someone upstream points it out for you.
Why BIN Attacks Trigger Acquirer Attention Faster Than Before
The reason BIN attacks escalate faster in 2026 has less to do with merchant performance and more to do with how risk is now governed upstream. Acquirers are no longer reacting only to losses. They’re reacting to patterns that indicate misuse of the network, even when every single transaction is declined.
Under Visa’s Acquirer Monitoring Program (VAMP), enumeration and card testing are no longer treated as peripheral signals. They sit alongside fraud and disputes as part of a consolidated monitoring view. That means acquirers are expected to notice and address behavioural risk, not just financial damage.
This shifts the escalation timeline in a subtle but important way. In the past, acquirers often waited for something tangible: rising chargebacks, confirmed fraud, issuer complaints. Now, repeated BIN-focused testing can be enough to prompt action because it indicates that a merchant environment is being used as a testing surface.
There’s also a governance angle. Acquirers sit directly between merchants and schemes, and VAMP makes it clear that acquirers are accountable for preventing sustained enumeration within their portfolios.
When BIN attacks appear, ignoring them isn’t a neutral choice. It creates programme exposure for the acquirer itself. That’s why conversations happen earlier and feel more urgent than merchants expect.
From the merchant’s side, this often feels unfair. Nothing went through. We blocked everything. There were no chargebacks. All of that can be true and still irrelevant. What matters upstream is whether the behaviour persisted long enough to be measurable and attributable. Once it is, acquirers are incentivised to intervene before thresholds are tested.
The practical result is a compressed feedback loop. BIN attacks that might once have lingered quietly for weeks now surface quickly, often framed around risk posture rather than incident response. For merchants, the implication is clear: waiting for carding to become obviously bad is waiting too long. In 2026, acquirer attention is triggered by patterns, not by damage.
Early Warning Signals Merchants Miss Until It’s TooLate
Most merchants don’t miss card testing because they’re careless. They miss it because they’re looking for the wrong kind of signal. Traditional fraud monitoring is still heavily outcome-driven approvals, losses, chargebacks. Carding doesn’t announce itself in those metrics anymore.
In 2026, the earliest signals of BIN attacks tend to sit between systems. They show up as small behavioural shifts that feel explainable in isolation but look very different when viewed together. Marketing teams see “odd traffic”. Fraud teams see “nothing converting”. Support sees nothing at all. Meanwhile, the pattern is forming.
What makes this dangerous is timing. By the time enumeration is obvious locally, it may already be visible upstream. Acquirers and schemes don’t need volume explosions to draw conclusions, persistence and structure are enough.
The warning signs merchants most often overlook include:
- Sudden concentration of attempts around a narrow set of BINs
- Issuer decline reason shifts that don’t align with campaign or UX changes
- Repeated credential permutations that never settle into real purchase intent
- Distributed retries that stay just below static velocity thresholds
Individually, each of these can look benign. Together, they describe traffic that is trying to learn, not buy.
Another blind spot is over-reliance on success metrics. Teams ask, Did anything get through? instead of What is this traffic optimising for? Card testing thrives in environments where failure responses are consistent and informative. A system that declines perfectly can still be doing attackers a favour.
The merchants that catch enumeration early are usually the ones asking uncomfortable questions. Why is this traffic here? Why does it behave differently from genuine users? Why is it persistent even though nothing converts? Those questions matter more in 2026 than whether fraud loss ticks up by a few basis points.
Missing these signals doesn’t mean you failed. It usually means your monitoring was built for yesterday’s threat model. Carding has moved on and the signals moved with it.
Why Traditional Fraud Rules Don’t Stop Card Testing
Most fraud rules are built to answer a simple question: should this transaction be approved?
Card testing isn’t interested in that answer.
That mismatch is why traditional controls struggle. Fraud engines optimise for outcomes approvals, declines, losses while carding optimises for feedback. A clean decline is still a result. A consistent error message is still information. Even a blocked transaction can confirm that a particular combination was worth trying.
This is where many merchants develop a false sense of security. Approval rates stay healthy. Chargebacks don’t move. Rules fire exactly as designed. On paper, everything works. But underneath, the checkout is behaving predictably, and predictability is exactly what testing scripts rely on.
Another limitation is scope. Fraud rules usually sit at the payment decision point. Card testing doesn’t. It probes earlier and wider: page loads, form behaviour, retries, authentication flows. If all of your intelligence lives at authority / decline, you’re only seeing a slice of the behaviour that matters.
There’s also a structural issue with optimisation. Fraud teams are often rewarded for blocking bad transactions efficiently. Card testing punishes that logic. Efficient blocking without behavioural disruption can actually accelerate learning. Attackers don’t need approvals if your system reliably tells them what failed and how quickly.
Finally, traditional rules assume intent. They assume a transaction is either fraudulent or genuine. Card testing sits in between. It’s not trying to complete a purchase, and it’s not trying to steal immediately. It’s experimenting. Most rule sets simply aren’t designed to reason about experimentation.
That’s why merchants who rely solely on fraud rules often end up confused when acquirers raise concerns. We declined; everything feels like a strong defence but under modern scheme scrutiny, it’s not enough.
In 2026, stopping card testing means going beyond decisioning and addressing how your system behaves when nothing is approved at all.
The Merchant Defense Playbook Without Turning This Into a Manual
The most effective merchant defences against card testing in 2026 don’t look like a checklist. They look like a series of design decisions that quietly change how attractive your environment is to test against. The goal isn’t to “win” against attackers. It’s to make learning expensive, slow, and unreliable.
Design Principle 1: Remove Predictable Learning Loops
Attackers thrive on consistency. Same response, same timing, same outcome repeatable signal. Many checkouts are unintentionally generous here. They retry automatically. They surface precise error states. They behave identically on the first failure and the tenth.
Strong environments break that loop. Failure handling becomes deliberately less informative. Retry paths exist, but they don’t behave like a clean experiment. From the outside, it becomes difficult to tell why something failed or whether the next attempt is worth making.
This isn’t about frustrating real users. It’s about ensuring that failure doesn’t translate into education.
Design Principle 2: Make Automation Expensive Before Payment Submission
A common mistake is focusing all defensive energy on the payment button. By the time a card is submitted, it’s often too late. Modern carding relies on automation that probes earlier layers: page loads, form behaviour, field validation, session persistence.
This is where baseline web resilience matters. Controls that slow down scripted interaction not by blocking outright, but by introducing friction and variability raise the cost of testing dramatically. Visa’s own guidance and broader industry standards consistently emphasise that merchants should not rely on payment-layer controls alone PCI SSC e-commerce best practices.
When automation struggles to move smoothly through your checkout, card testing loses efficiency long before it reaches authorisation.
Design Principle 3: Detect Behaviour, Not Just Outcomes
The strongest merchants stop asking whether transactions succeeded and start asking what the traffic is trying to do. Card testing has a different behavioural signature from commerce, even when individual attempts look normal.
That means paying attention to persistence, structure, and intent. Thin transactions that never evolve. Repeated permutations that don’t converge. Traffic that keeps returning despite never completing a purchase. These are learning patterns, not buying patterns.
Detection here isn’t about precision. It’s about recognising when behaviour stops making sense as commerce. Once you see that shift early, you can intervene long before acquirers or schemes need to.
The unifying theme across all three principles is intent. Good defence in 2026 isn’t reactive blocking. It’s designing systems that refuse to be good teachers.
When attackers can’t reliably learn from your checkout, BIN attacks tend to move on quietly, and without ever becoming someone else’s problem.
Preserving Conversion While Blocking Testers
This is where most merchants hesitate. They understand the risk of card testing, but they’re afraid that fighting it aggressively will punish genuine customers. Historically, that fear was justified. Heavy-handed controls used to mean broken journeys, abandoned carts, and support tickets.
The mistake is assuming that all friction is equal. It isn’t. Real customers and testing scripts respond very differently to selective resistance. Genuine users tolerate small inconsistencies if the journey still feels familiar and fair. Automation, on the other hand, depends on clean, repeatable behaviour. When that repeatability disappears, efficiency collapses.
Strong merchants design friction that’s situational, not global. Instead of slowing everyone down, they introduce variability where intent is unclear. Retry behaviour changes. Timing shifts. Error handling becomes less explicit. None of this feels dramatic to a human completing a purchase once. To a script running hundreds of permutations, it becomes costly and unreliable.
Another important distinction is visibility. Many merchants still surface too much information when things go wrong. Clear explanations help customers but they also help attackers optimise. The merchants that preserve conversion best are the ones that separate user reassurance from system feedback. Customers get confidence. Attackers get ambiguity.
It’s also worth reframing what conversion actually means in this context. Conversion isn’t just approvals. It’s sustained acceptance. If BIN attacks force acquirer intervention, tighten controls upstream, or degrade issuer trust, conversion suffers anyway just more slowly and with less control. Blocking testers early often protects revenue that would otherwise be lost later through declining acceptance.
The merchants that get this right stop asking, “How much friction can we afford?” and start asking, “Where does friction actually matter?” In 2026, preserving conversion doesn’t mean making your checkout easy to use. It means making it easy to buy and hard to learn from.
Stopping BIN Attacks Before They Reach Your Acquirer
This is the point where card testing stops being an internal annoyance and becomes a relationship problem. Once BIN attacks are visible to your acquirer, the tone changes. Conversations become formal. Timelines shorten. Tolerance drops. The real goal for merchants in 2026 is to intercept that escalation path altogether.
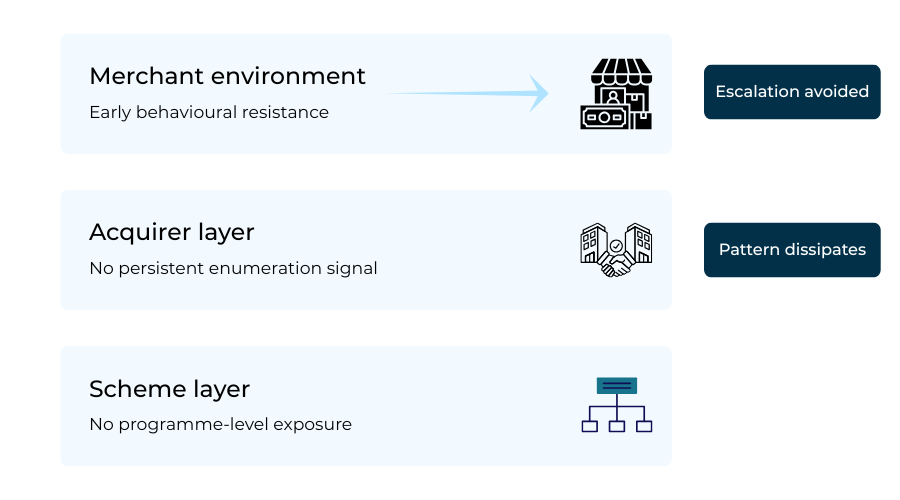
What makes the difference is timing. Acquirers usually get involved after patterns persist, not after the first burst of noise. Merchants who act early before testing traffic stabilises into a recognisable shape rarely end up in prolonged discussions. Those who wait for certainty often discover that certainty arrives too late.
The merchants that succeed here treat card testing as a continuity signal, not an incident. They don’t ask whether an attack “worked”. They ask whether their environment is becoming attractive to repeat testing. Once the answer starts leaning yes, they change the environment quickly, even if fraud losses are still zero.
From an acquirer’s perspective, this is exactly what they want to see. Not perfection, but awareness and control. Early intervention demonstrates that the merchant understands how enumeration risk is measured upstream and isn’t relying on the acquirer to absorb it.
This is also where documentation quietly matters. When merchants can show that they noticed abnormal BIN clustering early, adjusted behaviour, and saw testing dissipate, escalation often stops. Not because the attack never happened, but because the learning surface disappeared.
Stopping BIN attacks before they reach your acquirer doesn’t require heroics. It requires recognising that card testing is judged on patterns over time, not on individual transactions. When merchants design their defences with that reality in mind, most attacks burn out long before they become someone else’s problem.
What to Document When Card Testing Happens
When card testing appears, documentation isn’t busywork. In 2026, it’s part of how merchants protect their acceptance position. Acquirers don’t expect perfection, but they do expect evidence that you understand what happened and why it won’t persist.
The most useful documentation starts with time, not volume. When did the behaviour begin? How long did it last? What changed just before it appeared? Anchoring events to a clear timeline helps separate genuine incidents from ongoing environmental weakness.
From there, clarity matters more than detail. Acquirers are not looking for raw logs or screenshots. They want to see that you can describe the pattern in plain terms: which BIN ranges were affected, how behaviour differed from normal traffic, and why it didn’t represent real purchase intent. This shows comprehension, not just data access.
Equally important is what you changed. Merchants often overemphasise blocking actions (“we declined everything”) and underemphasise design changes. Acquirers care far more about adjustments that reduce learning opportunities, changes to retries, error handling, automation resistance, or flow behaviour. Those indicate forward control, not just cleanup.
Finally, there’s recurrence prevention. Not a promise, but a rationale. What would you notice sooner next time? Which signals are now monitored explicitly? How would you intervene earlier? Even a simple explanation here reassures acquirers that the same pattern won’t quietly rebuild.
Good documentation doesn’t need to be long. It needs to be credible. A short, coherent incident narrative does more to calm escalation than pages of metrics without interpretation. In 2026, the ability to explain card testing clearly is often what determines whether it remains an internal issue or becomes an acceptance conversation.
Conclusion
Card testing has outgrown its reputation as a niche fraud problem. In 2026, it sits squarely in the middle of merchant acceptance, acquirer governance, and scheme perception. BIN attacks don’t need to succeed financially to matter anymore. They only need to persist long enough to be measured.
That reality forces a change in mindset. Defending against carding is no longer just about blocking bad transactions. It’s about designing payment environments that refuse to act as learning surfaces. Predictable retries, clean error signals, and automation-friendly flows quietly create risk, even when fraud losses stay low.
Merchants that adapt early gain an advantage. They stop problems before they escalate, preserve trust with acquirers, and protect long-term conversion rather than reacting to sudden pressure. Those that don’t often discover that “we declined everything” is no longer a convincing explanation.
In 2026, card testing defence isn’t a bolt-on control or a specialist concern. It’s part of how acceptance is engineered and how continuity is maintained. Merchants that treat it that way rarely hear from their acquirer. Those that don’t usually hear from them sooner than expected.
FAQs
1. What is carding and how is it different from general fraud?
Carding, or card testing, is focused on validating card credentials rather than completing purchases. The goal is learning which cards work, not stealing funds immediately.
2. Are BIN attacks still common in 2026?
Yes. They’ve become quieter and more distributed, but BIN-range testing remains one of the most common ways attackers validate stolen card data.
3. Can card testing be a problem even if all transactions are declined?
Yes. Declines can still create measurable patterns. In 2026, behaviour matters as much as outcomes.
4. Why do acquirers care about failed card testing attempts?
Because schemes now treat sustained enumeration as ecosystem risk. Acquirers are accountable for merchants whose environments enable testing.
5. Is card testing mainly a bot problem?
Automation plays a role, but checkout design matters more. Predictable retries and clear error signals often do more harm than weak bot controls alone.
6. Does CAPTCHA stop BIN attacks effectively?
On its own, no. CAPTCHA can be bypassed or worked around. It’s only useful as part of broader automation resistance.
7. How quickly can BIN attacks escalate to acquirer attention?
Much faster than before. Persistent patterns can trigger attention even without fraud losses or chargebacks.
8. What’s the biggest mistake merchants make when responding to card testing?
Focusing only on blocking approvals instead of reducing learning opportunities in the checkout flow.
9. Do high-risk merchants face more pressure from BIN attacks?
Yes. Higher baseline scrutiny means less tolerance for enumeration noise and faster escalation.
10. Is card testing prevention a one-time fix?
No. Attack patterns evolve. Defence in 2026 is about ongoing design and monitoring, not a single rule change.
11. How should merchants explain card testing incidents to acquirers?
By clearly describing the pattern, the changes made to remove learning surfaces, and how recurrence will be detected earlier next time.
12. Why is card testing now considered part of acceptance strategy?
Because unchecked enumeration can degrade issuer trust, trigger programme scrutiny, and ultimately affect long-term acceptance and conversion.




